It has been half a century since the term "information society" was proposed in the latter half of the 1960s from the viewpoint that information has the same value as various resources.With the technological innovation of computers, active software development, and the development and spread of the Internet, all kinds of information have come to be digitized.
While digitalization has dramatically improved our living environment and improved convenience, the increase in cybercrime and its maliciousness and enormous damage pose a threat.Just as the Internet is indispensable to our lives in general, many means of cybercrime are due to the high degree of anonymity, the difficulty of leaving traces, and the fact that there are few restrictions such as geography and time. The Internet is the mainstream.
Cybercrime attacks vulnerabilities at a speed that is not noticeable, as if it were a blind spot or a surprise attack.Cyber groups will find invisible clues for any data that is strictly protected, so if it happens, the damage and damage will be immeasurable, and it will take some time to restore credit. ..
As DX promotion spreads for business support, efficiency, and competitive advantage, the handling of information should be strictly managed and observed.This time, we will focus on information security and introduce forensic (forensic) related software that is useful for investigating the causes of various incidents.
table of contents
Information Security Importance and Incidents
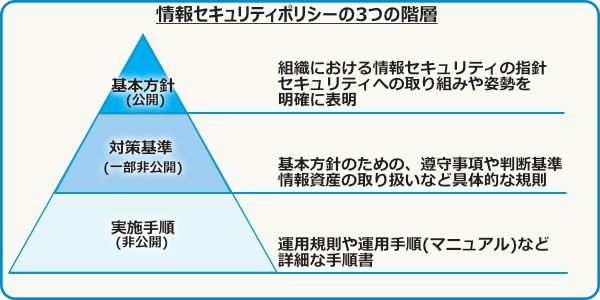
How to protect information assets from various threats, security measures (risk management) of information assets have become an important issue for companies and organizations.Companies and organizations are required to establish policies and action guidelines (information security policies) for information security measures to be implemented according to their business scale and system configuration.
The purpose of information security is to create an environment in which information (those with the same value as various resources) can be used safely and correctly at all times without problems.Although it is not the US Intelligence Agency (CIA), information security also has three elements called the CIA, each of which is "Confidentiality(Confidentiality) ""Completeness(Integrity) ""Usability(Availability) "is taken as an acronym.These three elements are also standard items in the certification of the international standard "ISO3", and it is important to secure these in a well-balanced manner.
Information security policy that shows the necessity of security measures and comprehensive, systematic and concrete
Measures for companies and organizations (Ministry of Internal Affairs and Communications)
https://www.soumu.go.jp/main_sosiki/joho_tsusin/security/index.html
Three elements of information security
1992, Organization for Economic Co-operation and Development (OECD, Organization for Economic Cooperation and Development) ByWhen the information security guidelines were established, there were three basic concepts to deepen the general understanding of information system security.Defined

・ What is confidentiality?
Only authorized (legitimate) people can access the data of interest
It is necessary to prevent incidents such as "information leakage" of corporate secrets due to unauthorized access or taking out, that is, in a state where confidentiality is not maintained.Ensuring confidentiality includes setting access rights, using passwords and encryption when sending files, and other measures against information leakage (including taking out and losing).
・ What is integrity?
The data is in the correct state (no missing or inconsistent)
Regardless of whether it is intentional or malicious, it is necessary to prevent incidents such as "tampering" in which data such as documents and records are rewritten at a timing other than the original update time.To ensure integrity, it is necessary to track the history of access detection and reorganization as a preventive measure against falsification for information integrity.
・ What is availability?
There is no problem with the system and the information can be used stably (useful).
It is necessary to prevent incidents that cause a physical failure of frequently accessed systems (servers, network devices, etc.) and make them unusable.To ensure availability, it is necessary to take measures in anticipation of system troubles (power supply measures, system duplication, backup, disaster recovery plans, etc.).
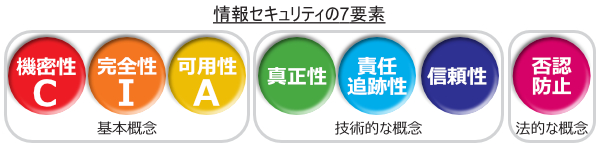
3 elements of information security next to 4 elements
In addition to the three basic concepts, the three elements of the technical concept "Authenticity(Authenticity) ""Responsibility traceability(Accountability) ""Reliability(Reliability) "and the legal concept"Non-repudiationWith the addition of (Non-repudiation), it is now called the Seven Elements of Information Security.
・ What is authenticity?
Information on entities (existential things, things, people) is as claimed
In online transactions that do not directly confirm the person's face, a third party illegally logs in using the information (ID, email address, password, etc.) owned by the person, and impersonates the person to make a transaction or post. Is listed as an incident.Preventive measures include digital signatures, two-step verification, and biometrics.
・ What is responsibility traceability?
Retroactively track when, who accessed and manipulated what information assets
It is important to obtain a digital certificate (certificate to prove that the person you are communicating with) and log information.
・ What is reliability?
There are no defects or defects in the processing by the information system, and the expected processing is surely performed.
If you are attacked by executing unintended processing or exploiting a vulnerability, it is important to prepare anti-virus measures, maintenance, and a system because the malicious intent may lead to loss of trust as well as corporate image.
・ What is non-repudiation?
Leave evidence to prevent denial or rumination after the fact
Log information includes information such as operation history, authentication status, access status, record of phenomena and events, and communication status.Responsibility traceability can be guaranteed by recording the digital certification and logs so that there are no defects.
In order to maintain an environment where you can always use it in a safe and normal state, it is important to recognize that there are possible problems and create an environment where problems are unlikely to occur.It is required to regularly review the system and operation method, and to establish measures (information security policy) for ensuring and strengthening information security, such as regular password changes and education on information handling. Has been done. ..
Digital forensics, a technology required to investigate the cause of an incident
Forensics is the process of forensics and investigation to find legal evidence, but it is the "digital data" for submission to the judiciary.A general term for means and technologies that clarify "legal evidence"Digital forensicsIt's called.
Examples of digital evidence that can be submitted as evidence (It may not be accepted depending on the specific case)
|
Digital forensics is used to investigate the cause of cybercrime or cyberattack damage (examples of security incidents: information leakage, spoofing, tampering, subsequent denial, wiretapping, etc.), or by law enforcement agencies such as police, judiciary, and government. Is the technology needed to collect, inspect, and analyze information that may be useful in criminal investigations and to find legal evidence.

See our guide to forensic techniques for incident response
Guide to Integrating Forensic Techniques into Incident Response (NIST, National Institute of Standards and Technology)
https://csrc.nist.gov/publications/detail/sp/800-86/final
Types of digital forensics
There are a wide variety of subjects that require forensics.Depending on the subject that needs analysis,Computer forensics""Network forensics""Mobile device forensics""Digital image forensics""Digital video / audio forensics""Memory forensicsThere is a name such as.I will summarize the three main ones.

・ Computer forensics
For computers, laptops (laptops), servers, removable disks (external hard disks and USB sticks)Identify, store, collect, and analyze the evidence found.
・ Network forensics
This includes firewalls, routers, peripherals, etc.Primarily look for worms, malware attacks (virus related), anomalous network traffic, and security breaches to discover sources of security attacks, intrusions, or other problem incidents.

・ Mobile device forensics
This applies to mobile phones, smartphones, SIM cards, PDAs, GPS devices, tablets, game consoles, etc.The main target is the recovery of electronic evidence.
Forensic tools
The basic configuration of forensic tools consists of four parts: identification, collection, inspection, and analysis.With the widespread use of computers, digital forensics is becoming more useful, allowing you to take advantage of the tools you need for quick recovery after an incident, or for law enforcement investigations and arrests (tools). There is no limit to the users who need it).
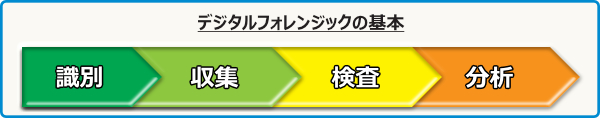
Here are some forensic tools.There are multiple options depending on the target, so I would appreciate it if you could refer to it.

All-in-one forensic tool for mobile devices
MOBILedit Forensic Express
Mobile phones and smartphones are representative of mobile terminals that are indispensable to our lives.Mobile device forensic tools specialized for this mobile deviceMOBILedit Forensic ExpressWith just a few clicks, you can extract data in your phone (call history, phonebook, text messages, multimedia messages, photos, videos, passwords, etc.) and create reports.
In addition to retrieving physical data, you can analyze applications that are constantly updated and recover forensic deleted data.
See NITS (National Institute for Standards and Technology) Mobile Device Forensic Tool Tests (Measurement Results).
Mobile device forensic tool test results performed by NIST
https://www.mobiledit.com/nist-repor
*This product is currently not available at our company.
Please contact the domestic distributor (Focus Systems Co., Ltd.) directly.
![]()
Software bundled with iOS-specific forensic tools
Elcomsoft Premium Forensic Bundle
The Elcomsoft Premium Forensic Bundle for law enforcement is a forensic tool for desktop and mobile devices.A value pack that bundles various functions such as password recovery, decryption and decryption of encrypted files, extraction of suspicious files, decryption and recovery, analysis, and report creation.
Among them, the iOS-specific iOS Forensic Toolkit is compatible with all generations of iPhone, iPad, iPad Pro, and iPod Touch, and unlocking and imaging functions are also available on legacy devices. * Most of the bundled tools are compatible with Windows and Mac.

Digital forensic software that is strong in web browsers
Net Analysis
Since it can be used anywhere with the Internet, an increasing number of companies are using Web systems as business tools.In addition to diagnosing application vulnerabilities, it is also necessary to consider information security during operation.
NetAnalysis is a forensic tool specialized for web browsers, and can extract, analyze, and report data (evidence) related to the activity of users of web browsers. Supports web browsers installed on Windows, Linux, macOS, iOS and Android.
The application HstEx included in NetAnalysis is a Windows-based multithreaded data recovery tool.For Windows, Linux macOS, Android or iOS systemsYou can recover deleted data from various internet browsers regardless of whether it is installed or not.

Fast password recovery, eDiscovery software
Passware Kit Forensic
Passware Kit Forensic includes password recovery for over 300 popular applications (such as Microsoft Office and Acrobat), as well as advanced features needed by specialized teams of digital forensics (forensic teams). It is useful for finding evidence by decrypting encrypted files and logs.
The Passware Kit is designed to apply all available computing resources for maximum efficiency and recover passwords instantly in batch mode.It supports NVIDIA (GTX, Tesla) and AMD GPUs, depending on the file type.

Software for digital forensic research
OSForensics
OSForensicsHas the ability to identify suspicious files and user activity inside your computer (such as the usage of accessed web browsers and event logs) and quickly extract evidence (forensic data) from your computer.
You can also organize all the evidence you find into one cryptographically secure case file, and manage your digital forensic investigations, including generating reports, adding external reports and evidence photos.
Extra – Software that records computer usage

ManicTime Pro
ManicTime Pro is software that can record the action history performed on the target computer such as the application and document to be used, the usage status of the Web browser, and visualize it as a timeline together with each work time.It is useful as a material for managing working hours and considering work efficiency.
This product is not a forensic tool, but from the perspective of information security responsibility traceability, for example, it is necessary to trace back when, who accessed and what information assets were accessed and operated. It may also be useful for the purpose of managing whether it is operated in the correct way on a regular basis.
Summary
We introduced forensic tools by looking at incidents such as information leaks that occur almost every day.As mentioned at the beginning, cybercrime is on the rise.Of course, it is best that no incidents occur, but as long as information is exchanged regardless of the size of the company, the possibility of being involved in a crime is not zero.We hope that this article will be of some help to you as a security measure and for prompt investigation of the cause in the unlikely event of an incident.
The following is a special feature of reverse engineering tools that are useful for security measures.Please refer if you like.
Our Overseas product procurement service for R & D "Unipos"We can help you with forensic investigations and information analysis to find legal evidence, and forensic tools for quick recovery in the event of an incident.Overseas forensics is more advanced than in Japan.If you have a product that is not yet available in Japan and you would like to obtain it, please feel free to contact us with information such as the product name and URL.We will check the availability and make a quote.